In crypto modules, an entity called software asks the module to do a cryptographic challenge. It’s like asking a helper to do a selected process.
Inside the international of crypto. Unique elements referred to as modules do critical jobs to hold matters comfortable. these modules use something referred to as cryptographic responsibilities to defend information. however, who tells these crypto modules what to do? It’s an entity that makes those calls. This entity gives the commands to perform these at-ease responsibilities. It’s like a boss telling employees what task to do. information this allows us to understand how our data remains secure.
What is a crypto module?
In crypto modules, the cryptographic engine performs cryptographic responsibilities. It uses algorithms to encrypt and decrypt statistics. The engine is referred to as using software program applications that want protection. these programs request encryption or decryption operations. The crypto module handles these requests securely. It ensures facts are protected for the duration of processing. The engine is vital for secure communications. It facilitates maintaining data confidentiality and integrity.
A variety of crypto modules exist, each with unique features. Numerous crypto modules are on the market, offering diverse functionalities.
- OpenSSL
- PyCrypto
- Crypto++
How Entities Interact with Cryptographic Modules
Entities like apps and systems use cryptographic modules to hold statistics securely. whilst those entities want to defend information, they make what’s referred to as a crypto call. A crypto call is a request to the cryptographic module to do something, like encrypt or decrypt statistics. that is much like how we name a pal to invite for help. The cryptographic module does the paintings and sends the result lower back.
What are crypto calls and how do they work?
Crypto calls are unique requests that inform the cryptographic module what to do. as an instance. If an app wants to disguise records so nobody can study them, it will make a crypto call to encrypt the statistics. APIs or software Programming Interfaces, are gear that help apps make those calls. They make it clean for apps to speak to crypto modules.
communication among entities and cryptographic modules takes place through those APIs. when an entity desires encryption, it sends a request using the API.
The API helps the cryptographic module apprehend what desires to be performed. This way, the entity and the module can work together easily. The module handles the request and performs the cryptographic task. Then, it sends the result lower back through the API. This method continues information and ensures that the entirety works efficiently.
Common Cryptographic Operations Performed by Entities
Within the world of cryptography, entities carry out important obligations to preserve facts securely. Encryption and decryption are two key jobs that entities handle. whilst records need to be saved mystery, entities call cryptographic modules to encrypt it.
Encryption turns information right into a mystery code. when the records wish to be used again, entities name the module to decrypt it. Decryption turns the secret code again into readable data. This enables preserving statistics that are non-public and secure.
Digital signatures and authentication.
Any other critical mission is virtual signatures and authentication. Entities use digital signatures to prove that statistics are proper and have not been changed. While you ship an e-mail or a message, entities use those signatures to ensure it is from the right character.
Authentication is like checking a password to make certain that the proper people can get the right of entry to the statistics. those actions make sure that communication is secure and truthful.
Security Considerations for Entities Calling Cryptographic Modules
When the use of cryptographic modules, protection could be very important. First, ensuring comfy entity authentication is prime. this indicates we want to make certain the entity requesting records is authorized to accomplish that. To verify this, we take a look at the identification of the entity earlier than processing their request. This helps in preventing unauthorized access and keeps the information safe.
Next, we ought to keep away from vulnerabilities in cryptographic calls. This includes following great practices to be comfortable with the operations. for example, continually use strong algorithms and keep the software program updated. keep away from unusual errors that could create weak spots. this could assist protect against assaults and keep the cryptographic module operating securely.
Eventually, compliance with cryptographic standards (FIPS a hundred and forty-2/3) is important. these standards set regulations for a way cryptographic modules must paintings. Following these regulations guarantees that the modules are examined and meet protection requirements. It allows for retaining trust and confidence within the cryptographic device.
Use Cases of Entities Calling Cryptographic Modules in Real-world Applications
Cryptographic duties in blockchain generation. Entities like miners and nodes use crypto modules in the blockchain. Miners assist with affirming transactions. They use cryptographic obligations to relax these transactions.
Nodes keep and confirm the information on the blockchain. they also use cryptographic duties to maintain the facts safe. This ensures that each transaction is at ease and trusted.
Web and application security (SSL/TLS encryption)
web sites and apps use SSL/TLS encryption to defend facts. while you visit a secure internet site, SSL/TLS encrypts the records between your browser and the website. This encryption is a cryptographic project.
It keeps your facts secure from hackers. programs use these cryptographic obligations to ensure that your data is covered for the duration of online activities.
Cloud services and cryptographic operations
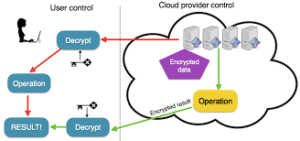
Cloud offerings additionally use cryptographic modules to shield facts. while you shop statistics within the cloud, it is encrypted.
Cloud-based entities name cryptographic obligations to preserve your facts secure. This guarantees that the best-authorized users can access your facts. Cryptographic obligations in cloud offerings assist keep the safety and privacy of your facts.
Future Trends in Cryptographic Entity Management
In the destiny, managing cryptographic tasks will become simpler with automation and AI. Artificial intelligence (AI) will help by automating cryptographic calls. because of this computer systems will do the paintings of encrypting and decrypting information quicker. AI could make these tactics greater green and accurate. It enables managing many responsibilities right away and keeps data secure.
Quantum-resistant cryptographic calls
Quantum computer systems are very effective and will destroy old encryption techniques. To live securely, new strategies known as submit-quantum cryptography are being advanced. these new strategies will shield information even from quantum computer systems. Entities will need to apply these new techniques to ensure their facts stay cozy.
Conclusion
In crypto modules, an entity calls the cryptographic engine to handle critical security responsibilities. This engine plays operations like encryption and decryption to preserve data security. when an utility desires to relaxed statistics, it sends a request to the crypto module.
The module then makes use of its algorithms to guard the facts. those calls ensure that sensitive data remains exclusive and intact. employing the usage of cryptographic modules, entities can safeguard their statistics from unauthorized access. The engine’s function is crucial in maintaining records’ safety and integrity. standard, information on how entities call those modules enables an appreciation of the importance of cozy communique and data protection.